PicoCTF: Who are you? {Medium} {Web exploitation}
Overview
Below is a writeup for the picoCTF “Who are you?” challenge in the web exploit category.
Solution
- 1️⃣ Upon loading the initial site the page displays the message that only official ‘PicoBrowser’ users are allowed to visit the site. This led to me realising that Burp Suite was likely needed to modify the initial HTTP request to the site.
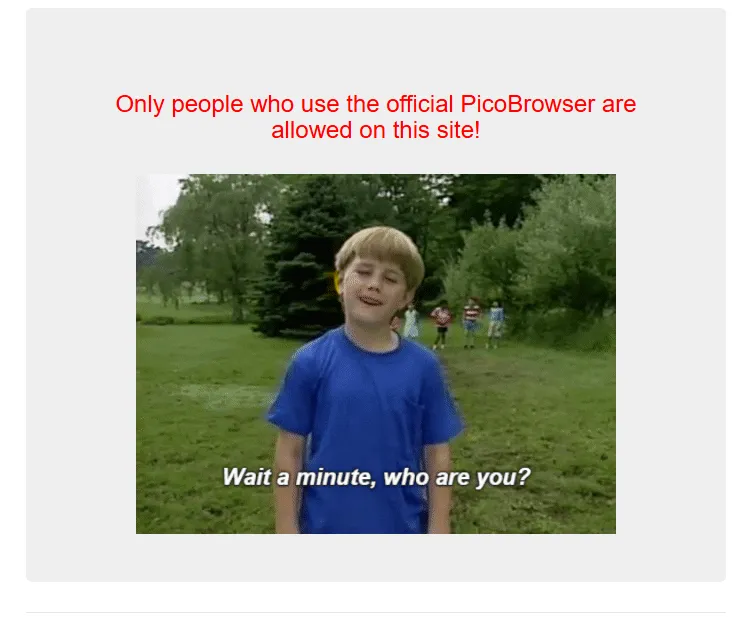
- Within Burp I modified the user agent to mimic the connection coming from the pico browser.
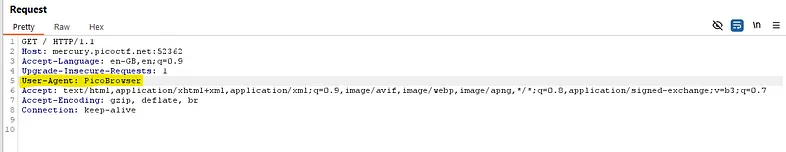
- 2️⃣ After modifying the UA and forwarding the request I was then presented with a new message on the site.
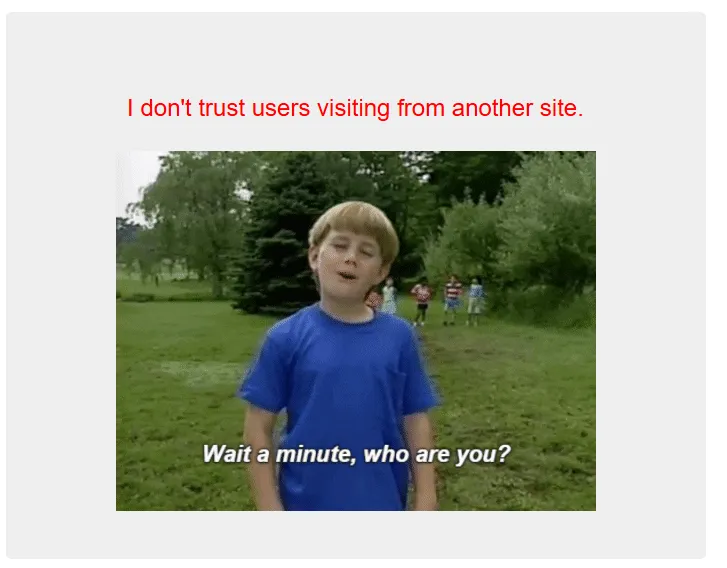
- This was a reference to the “referer” policy so by simply setting this to the origin domain it should accept this connection.
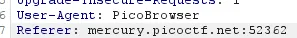
- 3️⃣ After sending the previous request this then presented a new output.
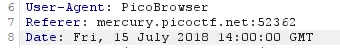
- To bypass this I set the “Date” header to a date from 2018 along with the other http header arguments from the previous steps.
- 4️⃣ Once again a new output message was present indicating the previous attempts were successful but there was still more steps to go.
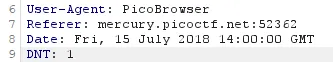
- Initially, this message stumped me as I was unsure what header related to this message. After researching (https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/DNT) I managed to stumble across the “DNT” header which is used to indicate a user’s tracking preferences. By setting this value to “1” it would set it so the user doesn’t want to be tracked. Adding this into the burp intruder along with the previous arguments again to attempt to bypass this message.
- 5️⃣ After this was successful the new message below was presented.
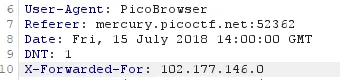
- From pre-existing knowledge I knew the “X-Forwarded-For” header could be employed along with a Swedish IP address.
- Taking an IP address from { https://lite.ip2location.com/sweden-ip-address-ranges?lang=en_US } I was able to pass this with the other headers.
- 6️⃣ A new message (the final message) was returned after sending the request which implied the “Accept-Language” header was required
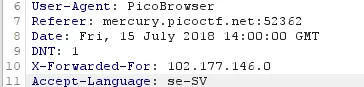
- I used the header name and country to find the relevant parameter “se-SV” and passed this final header along with all the rest to receive the output
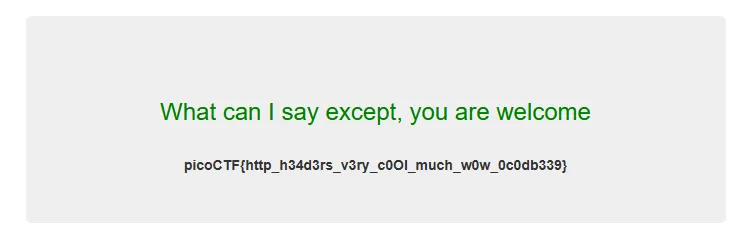
Final flag
- 🚩 picoCTF{http_h34d3rs_v3ry_c0Ol_much_w0w_0c0db339}
