Unpacking brbbot: Dissecting a persistent, covert botnet malware.
Overview
- Sample Name/Label: brbbot malware
- Date of Analysis: 19-05‑2025
- Summary: brbbot (part of brbbot malware family) is a botnet malware to allow attackers access to systems. The malware uses basic anti-debugging, drops an encrypted config file, and communicates with a hardcoded domain to exfiltrate system metadata.
Sample Information
A baseline of all static identifiers.
| Field | Value |
|---|---|
| Filename | brbbot.exe |
| Size | 75776 |
| MD5 | 1c7243c8f3586b799a5f9a2e4200aa92 |
| SHA‑256 | f47060d0f7de5ee651878eb18dd2d24b5003bdb03ef4f49879f448f05034a21e |
| File Type | PE32+ |
| Timestamp | 2015-02-25 06:12:18 |
Static Analysis
- Loaded the sample into peframe to analyse for potentially suspicious imports, and identify hints of obfuscation or packing.
- Notable behaviour details:
-
IsPE64, anti dbg, Xor, IsDebuggerPresent - Notable strings:
Software\Microsoft\Windows\CurrentVersion\Run- Likely persistence mechanism.-
Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1; Trident/4.0)- UA for network activity. -
Notable Imported DLLs:
-
ADVAPI32.dll– Registry manipulation, service management. -
WININET.dll– Create internet requests. -
WS2_32.dll– Socket creation for outbound requests.
-
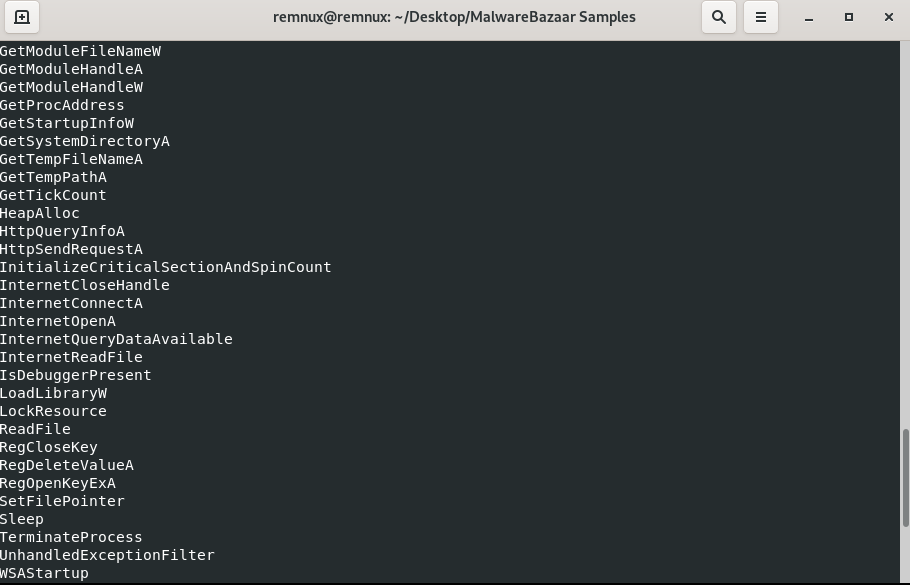
The above noteworthy DLLs can be seen being used within the below API calls of the program to initiate internet connections and manipulate registry keys.
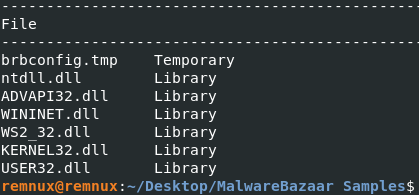
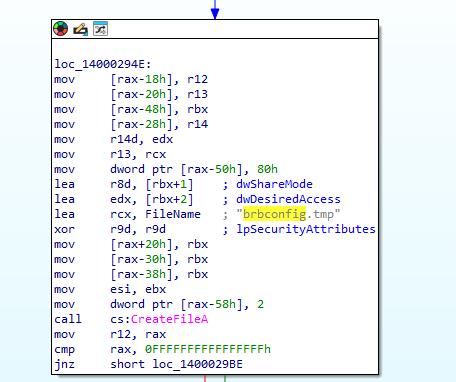
peframe also identified that a .tmp file is present in this executable named ‘brbconfig.tmp’ which is worth noting as it is highly likely this file will be dropped during execution.
Control‑Flow & Function‑Level Inspection (IDA)
- Decompiled View:
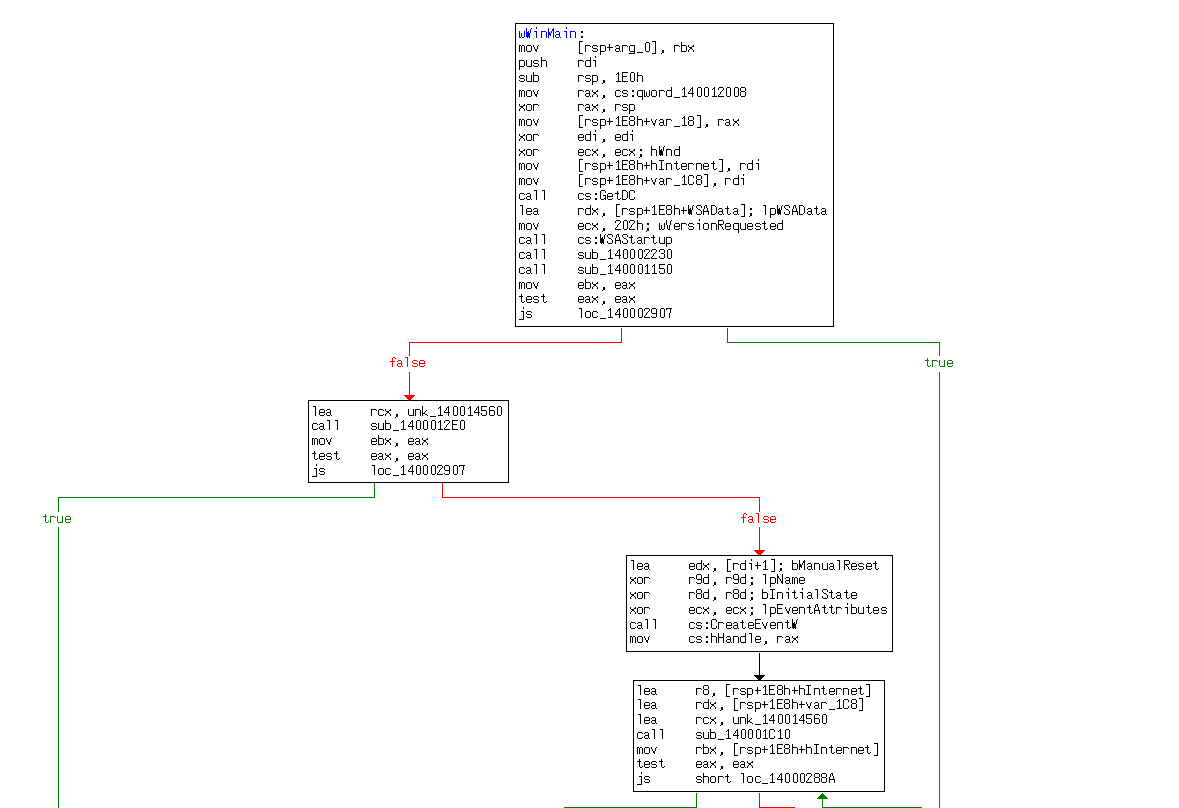
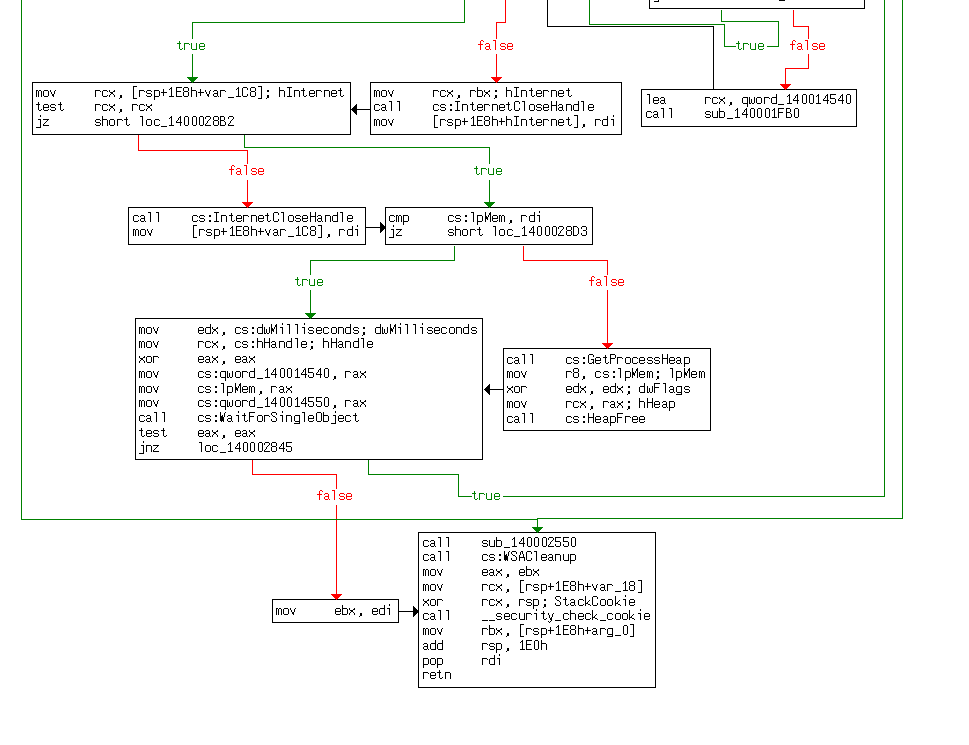
Now as we previously saw during the command line static analysis stage, a file called “brbconfig.tmp” is created and dropped by the executable. Knowing this we can search for “config” to try and find the relevant functions that create this encrypted file.
This successfully found a function that contained the details of the tmp file.
As this is still practice for myself, a deep dive into the construction/decryption of this encrypted dropped file can be found here:
https://ry0dan.github.io/malware%20analysis/in-depth-analysis-of-brbbot/
Dynamic analysis
To begin we execute the malware sample in an isolated environment and monitor for the below changes…
- Files created by malware
- Changes made in the system
- IPs/Domains connected
- Registry changes
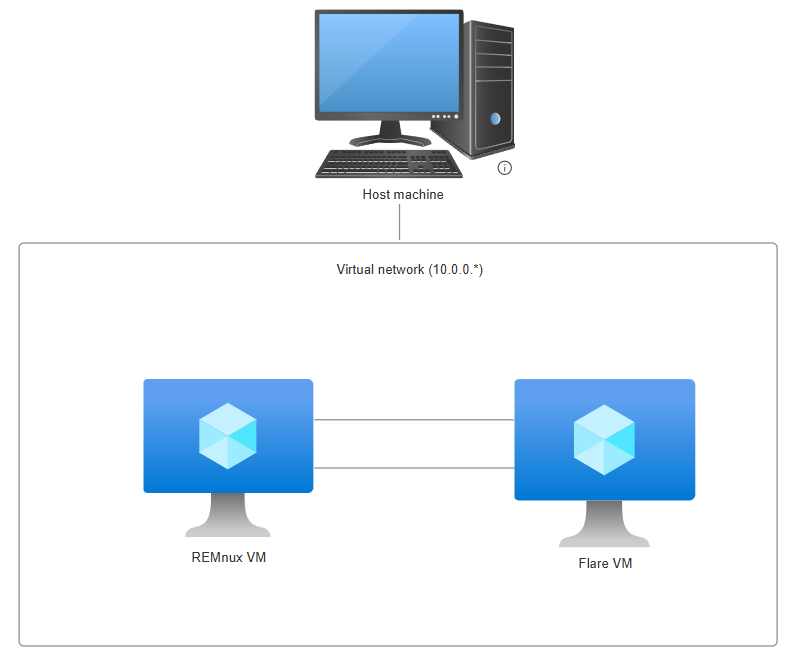
A screenshot of the analysis environment I’m using can be found below, this will also be the same for all my subsequent malware analysis writeups.
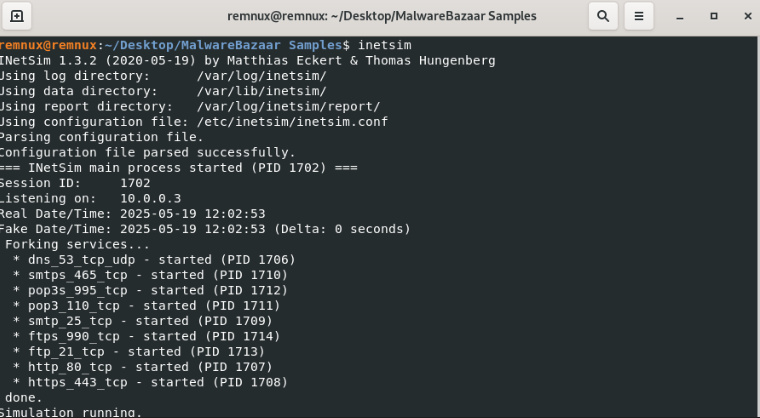
Firstly we will start by using inetsim which will respond to the malware network requests with a dummy response. This can be started up by simply entering ‘inetsim’ into the terminal (on remnux machine).
Now on the flare-vm we will begin running procmon to help give a visual representation of the malwares execution revealing if the malware creates any new or child processes. Alongside this Wireshark was also used to help monitor the network traffic activity. Now it was time to detonate the malware.
Once detonated the below filter was used in process monitor to examine the relevant operations.
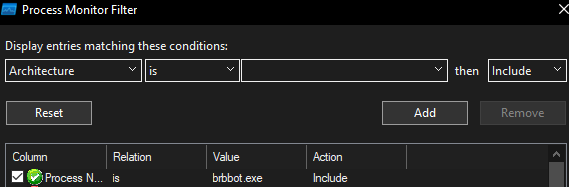
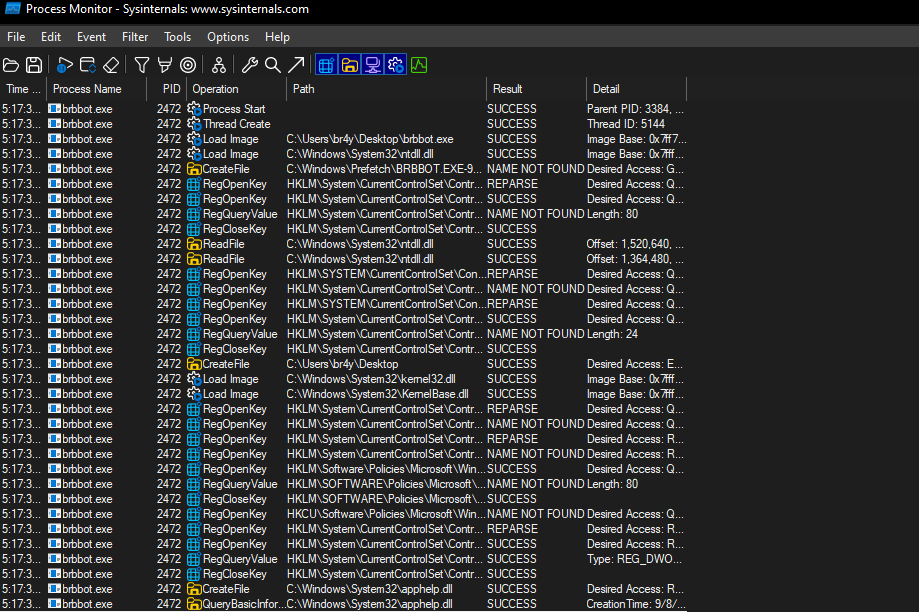
This produced numerous results which demonstrated several registry edits taking place:
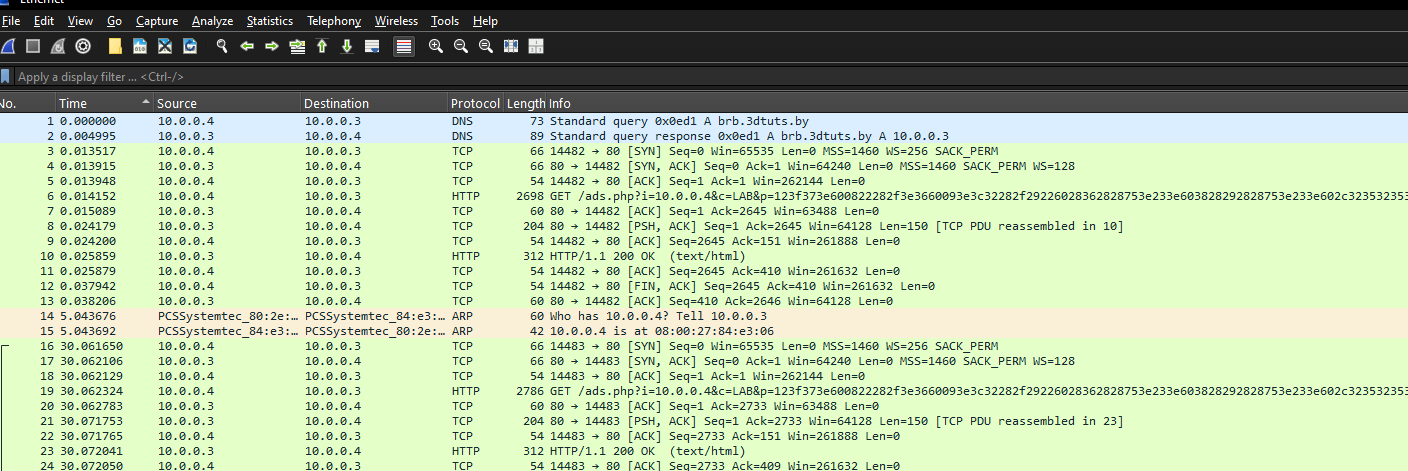
Within Wireshark we also captured the network activity taking place:
Observations:
- Malware is making an outbound connection to a C2 server brb.3dults[.]by
- VM tries to connect the C2 IP by initiating a TCP handshake
- In packet 6 we can see a GET request with parameters being passed to it. First the IP address which in this case is the internal 10.0.0.4 IP address. Then the hostname which in this case is “LAB”. Finally the user agent which we previously pulled out using strings (Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1; Trident/4.0))
- The malware is also seen making changes to the registry in attempts to gain greater persistence on the infected system. It does this by setting up new values for proxy bypass, accessing internet cache, disabling auto detect.
Indicators of Compromise (IOCs)
-
File Hashes:
-
MD5: 1c7243c8f3586b799a5f9a2e4200aa92
-
SHA‑256: f47060d0f7de5ee651878eb18dd2d24b5003bdb03ef4f49879f448f05034a21e
-
-
Files dropped:
- C:\Users\USER\AppData\Roaming\brbconfig.tmp
-
Registry Keys:
- Software\Microsoft\Windows\CurrentVersion\Run
-
Network IOCs:
-
brb.3dtuts.by
-
1855.84.108.232
-
Defence & Mitigation Recommendations
-
Detection: Deploy detection rules that monitor for any of the listed IOCs along with the mechanisms of this malware.
-
Prevention: Block known C2 domains at proxy.
-
Response: Audit systems for registry run‑keys and dropped files in.
-
Hunt: Search logs for IOCs in the section above.
Thank you for reading!
